4 Things Industry 4.0 01/05/2026

Presented by

Happy January 5th, Industry 4.0!
Welcome to 2026. If you're anything like us, you spent the last week somewhere between "new year, new me" ambition and "I'll start Monday" energy. Either way, you're here now — and there's no better way to kick off the year than digging into what's actually shaping the future of manufacturing and tech.
2025 was a whirlwind but a great year, and we're ready to make 2026 even better. Here at 4.0 Solutions we have several big things planned, including a new ambitious project launch, a new Digital Factory Mastermind Curriculum, and much more. And don't forget the ProveIt! Conference in February, which is bigger and better than last year!
And for all our new year resolutioners, those who've made their goals to improve their operations, we're providing 25% off everything at IIoT University with the code NEWYEAR, as both a thank you and to help get your manufacturer to where you're trying to go.
All that being said. this week we're covering Microsoft finally pulling the plug on a 26-year-old encryption relic, how AI is turning software itself into an industrialized commodity, a full retrospective on 2025's LLM landscape, and a practical deep-dive on managing fleets of edge AI devices at scale.
So shake off the holiday fog, refill that coffee, and let's get into what matters for the factories, platforms, and systems you're building this year.
Microsoft Will Finally Kill RC4 — The 26-Year-Old Encryption Relic Hackers Love

After 26 years, Microsoft is finally pulling the plug on RC4 as the default encryption method in Active Directory — and if you're running Windows-based infrastructure in your plant, this one matters.
What's changing:
RC4 (Rivest Cipher 4) has been baked into Active Directory since its launch in 2000. While Microsoft added support for the much stronger AES encryption standard years ago, Windows servers have continued responding to RC4-based authentication requests by default. That fallback has been a goldmine for attackers using a technique called "Kerberoasting" — extracting encrypted credentials and cracking them offline. RC4-encrypted tickets can be cracked hundreds of times faster than AES-protected ones.
By mid-2026, Microsoft will change the default on Windows Server 2008 and later to only allow AES-SHA1 encryption. RC4 will still exist, but it'll be off unless an admin explicitly re-enables it.
Why this matters for manufacturing and industrial networks:
If your plant runs Active Directory — and most do — this is directly relevant. The Ascension healthcare breach last year, which disrupted 140 hospitals and exposed 5.6 million patient records, was tied to RC4 vulnerabilities. Industrial networks with IT/OT convergence face the same risks: an attacker who cracks service account credentials can move laterally into SCADA systems, historians, or anywhere else those accounts have access.
What you should do now:
Microsoft is releasing PowerShell scripts and KDC log updates to help identify RC4 usage lurking in your environment. Legacy systems — including some third-party industrial software — may still require RC4 and could break when the default changes. Start auditing now, not in Q2 2026.
👉 Read the full story: https://arstechnica.com/security/2025/12/microsoft-will-finally-kill-obsolete-cipher-that-has-wreaked-decades-of-havoc/
The Rise of Industrial Software — When Code Becomes a Commodity
For most of its history, software has been closer to craft than manufacture: costly, slow, and dependent on skilled humans. AI coding is changing that — and the implications mirror what happened when physical manufacturing went through its own industrial revolution.
The shift:
Chris Loy's recent essay argues that AI-assisted coding is industrializing software production itself. Just as automation in manufacturing reduced reliance on human labor while dramatically increasing output, AI coding tools are collapsing the cost of producing working software. The result? A new class of "disposable software" — code created with no expectation of long-term ownership, maintenance, or deep understanding.
Advocates call it "vibe-coded software." Critics call it "AI slop." Either way, the economics are undeniable: when production gets cheap enough, volume wins.
Why this matters for Industry 4.0:
If you've spent any time in manufacturing, this pattern is familiar. Industrialization doesn't just make good products cheaper — it creates economic pressure toward high-volume, low-quality output. Think ultraprocessed food, fast fashion, or disposable consumer electronics. Loy draws the parallel directly: just as industrial agriculture gave us both abundant food and a diabetes crisis, industrial software may give us abundant applications and a technical debt crisis.
For manufacturers building digital infrastructure — UNS architectures, edge analytics, MES integrations — the question becomes: when do you leverage cheap, AI-generated code, and when do you invest in durable, human-designed systems? The answer probably isn't "always one or the other."
The deeper question:
Loy's most provocative point: "Technical debt is the pollution of the digital world, invisible until it chokes the systems that depend on it." In an era of mass automation, the hardest problem isn't production — it's stewardship. Who maintains the software that no one owns?
For industrial systems expected to run for decades, that's not a philosophical question. It's an operational one.
👉 Read the full essay: https://chrisloy.dev/post/2025/12/30/the-rise-of-industrial-software
2025: The Year in LLMs — A Practitioner's Retrospective
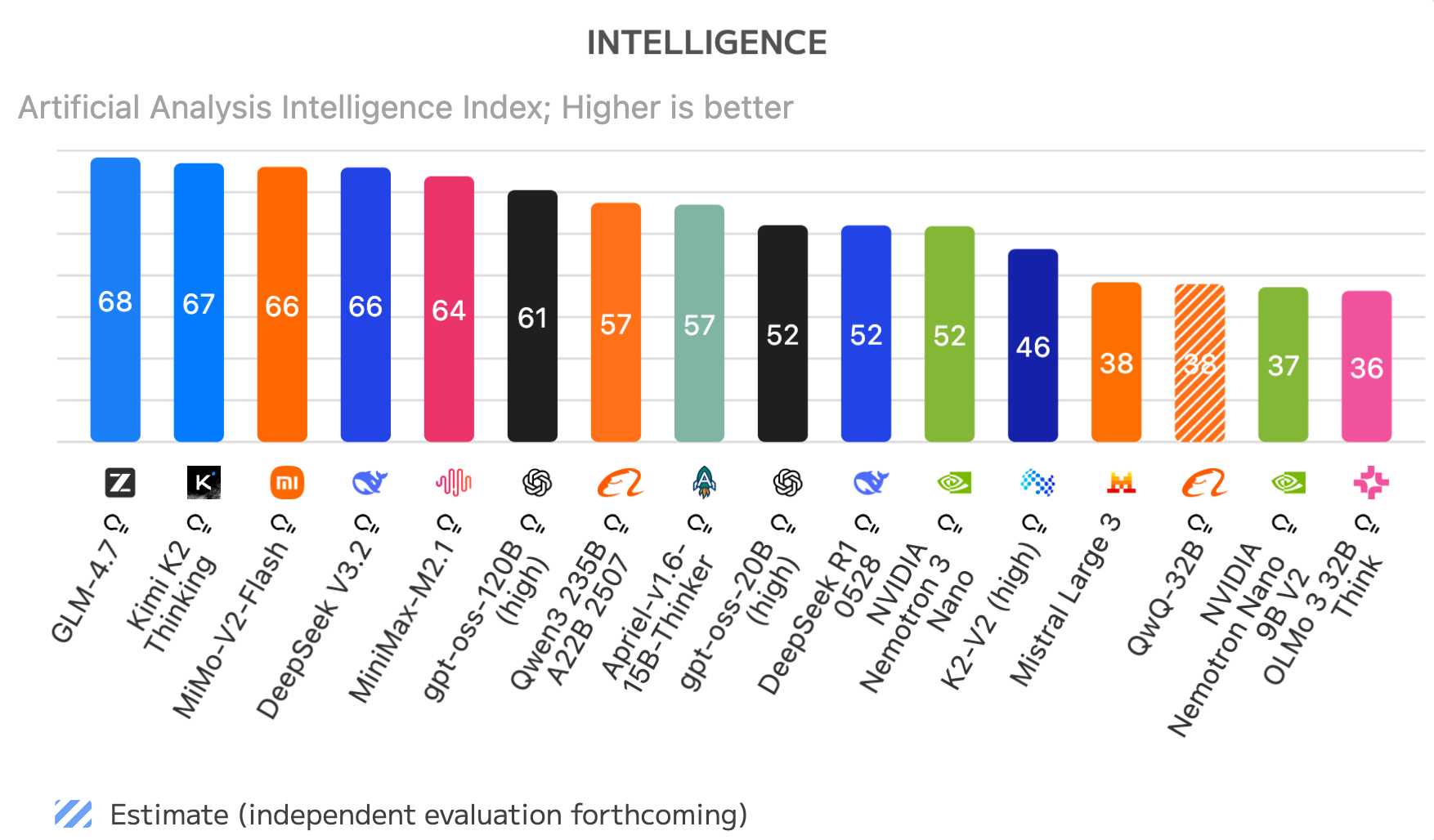
Simon Willison's annual "year in LLMs" post has become essential reading for anyone building with AI. His 2025 edition is the most comprehensive yet — and for Industry 4.0 practitioners, it's packed with insights that matter.
The headlines:
- Reasoning models went mainstream. The "o1-style" inference-scaling trick spread to every major lab. The real unlock? Reasoning models are exceptional at driving tools — planning multi-step tasks, executing them, and adapting based on results. AI-assisted search and code debugging finally work reliably.
- Coding agents became real. Claude Code, Codex CLI, Gemini CLI, and a dozen others emerged. These aren't chatbots — they're systems that write code, run it, inspect results, and iterate. Anthropic credits Claude Code with $1B in run-rate revenue. A CLI tool.
- Chinese open weight models surged. DeepSeek, Qwen, Kimi, GLM, MiniMax — the top-ranked open weight models are now predominantly from Chinese labs, often under MIT or Apache 2.0 licenses. For edge deployments and cost-sensitive industrial applications, this matters.
- Long tasks got longer. METR's research shows models can now complete tasks that take humans 5+ hours. The length of tasks AI can handle is reportedly doubling every 7 months.
- MCP might already be fading. Willison argues that coding agents with Bash access can do anything an MCP server can — and Skills (Markdown files with scripts) may be the simpler, better pattern. Worth noting for anyone deep in MCP architecture right now.
Why this matters for manufacturing:
If you're building industrial AI systems, integrating LLMs into operations, or just trying to understand where the tools are headed, this retrospective is the single best summary of the year. Willison's perspective is practical — he's building with these tools daily, not just writing about them.
The security sections are particularly relevant: the "lethal trifecta" (agents with private data access, external communication, and untrusted input) and the "normalization of deviance" around YOLO mode are warnings worth heeding before deploying agents in production environments.
👉 Read the full retrospective: https://simonwillison.net/2025/Dec/31/the-year-in-llms/
A Word from This Week's Sponsor

HiveMQ continues to lead the industry in reliable, scalable, secure industrial data movement — enabling teams to connect OT and IT systems with confidence. At ProveIt! 2025, they stole the show with the launch of HiveMQ Pulse, an observability and intelligence layer designed specifically for MQTT-based architectures. It was the biggest announcement of the conference — and Pulse is already proving to be a transformative tool for anyone building real-time, UNS-driven systems.
In 2026, folkss will get to see Pulse in full effect, along with HiveMQ’s continued innovations in:
-
High-availability, enterprise MQTT clusters
-
Real-time UNS data flow and governance
-
Deep visibility into client behavior, topic performance, and data reliability
-
AI-assisted operational insights
HiveMQ is not just a broker — it’s the data infrastructure layer enabling scalable digital transformation, advanced analytics, and the next generation of industrial AI.
We’re proud to feature HiveMQ as our newsletter sponsor and as a Gold Sponsor for ProveIt! 2026.
👉 Learn more about HiveMQ at HiveMQ.com
Or Get Started for Free: https://www.hivemq.com/company/get-hivemq/
How Kairos Solves the Edge AI Fleet Management Problem

Managing a global fleet of AI-powered edge devices is one of the hardest operational challenges in industrial IoT. Aurea Imaging, a Dutch agricultural tech startup, just published a detailed case study on how they solved it — and the architecture patterns are directly applicable to any manufacturer running edge compute at scale.
The problem:
Aurea runs NVIDIA Jetson-powered remote sensing devices on tractors in agricultural fields worldwide. These devices run machine learning inference for crop-level precision agriculture. The challenge? Keeping a distributed fleet up-to-date — not just at the application level, but at the host level: JetPack, CUDA, firmware, peripheral drivers, the whole OS.
When your devices are mounted on equipment in fields with flaky connectivity, traditional update approaches don't work. And when something goes wrong, you can't just send a technician to a farm in another country.
The solution:
They adopted a cloud-native approach: K3s (lightweight Kubernetes) on the edge, combined with Kairos — a CNCF Sandbox project that converts Linux distributions into immutable, image-based operating systems.
The key benefits:
- Atomic, image-based upgrades. Instead of updating packages in place, the entire OS image is replaced. No partial states, no drift. If something fails, automatic rollback to the previous working image.
- No more "snowflake" devices. Before Kairos, every device had slightly different packages and drivers. Troubleshooting was inconsistent. Now the fleet is homogeneous — same image everywhere.
- Remote Day-2 operations. Firmware fixes, driver updates, even base OS changes can be pushed remotely to the entire fleet simultaneously. No physical access required.
- Faster provisioning. New devices get pre-flashed with the Kairos image. Provisioning no longer involves package installation steps — just cloud resource generation and certificate copying.
Why this matters for manufacturing:
If you're deploying edge AI — whether for vision inspection, predictive maintenance, or real-time analytics — fleet management is the unglamorous problem that will eventually bite you. The patterns here apply directly:
- Immutable OS images eliminate configuration drift across devices
- A/B upgrade schemes prevent bricked devices in the field
- Containerized applications on top of K3s give you the same deployment patterns as cloud infrastructure
- The whole stack can be maintained with a Dockerfile — CUDA binaries, custom firmware, device drivers, all version-controlled and reproducible
Aurea's devices need to last a decade (typical agricultural equipment lifecycle). Having control of both application and host-level software makes that commitment achievable without field replacements.
👉 Read the full case study: https://www.cncf.io/blog/2025/12/29/how-to-integrate-kairos-architecturally-into-an-edge-ai-platform/
Learning Lens

New Year, New Skills — 25% Off Everything at IIoT University
If "level up our operations" made it onto your 2026 goals list, here's the push you need to actually make it happen.
Digital transformation doesn't start with a platform purchase or a vendor contract. It starts with education — understanding the architecture patterns, the integration strategies, and the operational realities that separate successful implementations from expensive disappointments.
That's why we're kicking off the new year with 25% off everything at IIoT University — courses, workshops, and yes, the Digital Factory Mastermind program.
Why this matters:
The gap between manufacturers who are thriving with Industry 4.0 and those still struggling isn't budget or technology — it's knowledge. The teams that understand UNS architecture, know how to scope an integration project, and can speak the language of both OT and IT are the ones actually shipping results.
Whether you're an engineer trying to build the business case for your first UNS pilot, a leader trying to upskill your team, or someone who's been meaning to dig deeper into MCP and agentic AI — there's no better time than right now.
New year. New skills. Same mission: get your plant to where it needs to go.
Use code NEWYEAR at checkout for 25% off any product.
👉 Browse courses and programs at IIoT University
Byte-Sized Brilliance
The Most Dangerous Week in IT
Statistically, the first full week of January is when the most passwords get reset across enterprise systems. Why? Because after two weeks of holiday brain, nobody remembers what they changed right before vacation "for security reasons."
The real kicker: a surprising number of those resets happen on systems that control actual physical equipment. Somewhere right now, a maintenance tech is standing in front of an HMI, coffee in hand, trying "Winter2025!" for the third time before triggering a lockout.
If your SCADA system has a "forgot password" option that emails a reset link... maybe check on that.
|
|
|
|
|
|




Responses